Cybersecurity Frameworks: A Comprehensive Guide
The Complete Guide to Understanding Cybersecurity Frameworks
What is a cybersecurity framework? A Cybersecurity framework is a set of controls that, when met, represents a fully functional cybersecurity program. The two most common cybersecurity frameworks are the NIST Cybersecurity Framework and ISO-27000, although there are dozens of different frameworks that serve the needs of different industries. Some frameworks are focused around specific industries, while others just vary in wording and controls. 84% of organizations in the US utilize a cybersecurity framework, and 44% use more than one, according to Tenable. At Celerium, we recommend focusing on the NIST Cybersecurity Framework, which is widely considered to be the gold standard for building a cybersecurity program. So let’s dive right into some specific cybersecurity frameworks. When considering cybersecurity framework’s we also recommend taking third-party vendors into account. Many frameworks either explicitly or implicitly deal with third parties. For more information about third-party risk management and how to fit it into your program, we recommend taking a look at this post.
NIST
NIST stands for the National Institute of Standards and Technology and is a government-funded entity that has promulgated several different cybersecurity frameworks. There is the NIST Cybersecurity Framework, NIST 800-53 rev4, and NIST 171. While these three frameworks share most elements in common, there are some minor differences in structure and controls based on their specific use cases. So let’s go over each in turn.
The NIST Cybersecurity Framework is the broadest of these frameworks and is meant to apply to any organization looking to build a cybersecurity program. The security controls in the framework are broken up into 5 key functions. These functions are: Identity, Protect, Detect, Respond, and Recover. According to Tenable’s survey of IT Professionals, 70% said they adopted the NIST CSF framework because they consider it a best practice.
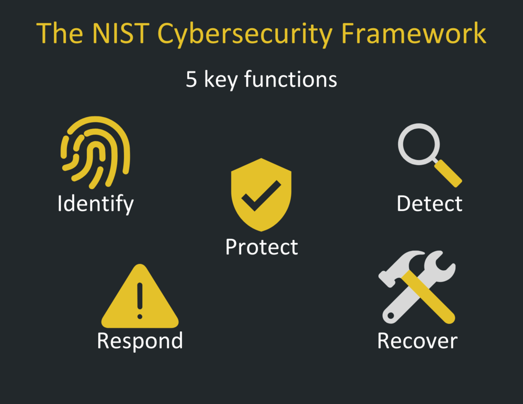
- Identify: Identify is focused on laying the groundwork for an effective cybersecurity program. Controls in this group include conducting a risk assessment, inventorying IT assets, and creating a comprehensive risk management strategy. By identifying risks and documenting where sensitive data is stored, your organization can ensure controls are effectively implemented to protect the most critical business processes and most valuable data.
- Protect: The protect function involves implementing technology and creating processes to ensure the adequate protection of data. These controls include providing employees with security awareness training, and employing protective technologies such as anti-virus and access controls.
- Detect: Detecting potential cybersecurity incidents is critical. Many companies only find out they have been breached when their proprietary or customer information is sold on the dark web. The Detect function of the NIST Cybersecurity framework involves controls designed to ensure your organization detects potential incidents when they occur.
- Respond: No matter how good your cybersecurity posture is, incidents can still happen. Controls found in the response function focus on ensuring that your organization has the capacity to rapidly and efficiently respond to a cybersecurity incident. When an incident occurs, seconds matter.
- Recover: Recovering from a cybersecurity incident can be tough. You have to worry about managing brand reputation, restoring functionality to IT assets, and ensuring that your systems are clean. Controls in the Recover function cover lessons learned, planning for recovery before the incident, and testing recovery processes.
Unless a specific framework is mandated by their industry or regulatory body, most companies should focus on following the NIST Cybersecurity Framework. It is comprehensive, understandable, and meets many compliance requirements by default. By following the NIST Cybersecurity Framework, you can be confident that you are adhering to cybersecurity best practices.
NIST 800-53
NIST 800-53 is a framework that is specifically designed to apply to U.S. Federal Government agencies. Compared to the NIST Cybersecurity Framework, NIST 800-53 is over 10 times as long (453 pages compared to the NIST Cybersecurity Framework at 41 pages. NIST 800-53 is broken down into the following families:
Access Control: These controls are focused around ensuring that only authorized users are able to access critical systems and information.
Awareness and Training: The Security Awareness and Training family of controls mandate that end-users (employees) are trained in how to properly prevent, detect, and respond to cybersecurity incidents.
Audit and Accountability: These controls are designed to provide records for auditors to understand and hold users and administrators accountable for maintaining cybersecurity.
Configuration Management: Configuration management involves configuring information systems to have optimal security. Controls include change control and security impact assessments, among others.
Contingency Planning: This family involves planning for incidents and contingencies to allow for optimal response.
Identification and Authentication: The Identification and Authentication family is designed to ensure that users are correctly authenticated when using networks or accessing sensitive data. Controls include the types of authentication to be used, encryption, and policies and procedures regarding authentication.
Incident Response: The Incident Response family focuses on ensuring processes are in place for quickly responding to and remediating incidents. Controls include incident response training, incident handling, monitoring for incidents, and incident handling among others.
Maintenance: This family is focused on ensuring that systems are adequately maintained. Controls include timely maintenance, controlled maintenance, and nonlocal maintenance.
Media Protection: The Media Protection family involves controls that are designed to protect media, including stored media, media access, and media sanitization.
Physical and Environmental Security: Physical and Environmental Security is just as it sounds. This family of controls is less to do with cybersecurity and includes items such as disaster recovery planning, emergency power, emergency lighting, and Fire Protection.
Planning: Planning is critical for cybersecurity. Planning in NIST 800-53 involves controls around creating a system security plan, rules of behavior, and information security architecture.
Personnel Security: This family deals with security issues arising from personnel present at the facility and includes controls such as screening, termination, and policies and procedures around personnel.
Risk Assessment: This set of controls designates how a Risk Assessment should be performed, policies for performing the risk assessment, and vulnerability scanning.
Systems and Services Acquisition: These controls deal with System Development Life Cycle, Acquisition Process, and Information System Documentation, among others.
Systems and Communications Protection: These controls are designed to mitigate risks from common cyberattacks such as distributed denial of service and malware. They include encryption, segmentation, VoIP security, and others.
Systems and Information Integrity: These controls are focused on ensuring the integrity of organizational information systems. Controls include error handling, spam protection, memory protection, and fail-safe procedures, among others.
As mentioned, NIST 800-53 was built for government entities. However, if you run a large enterprise and need a detailed standard for building a cybersecurity program, you really can’t do better. NIST 800-53 provides granular detail for each control that needs to be implemented to ensure that you have a comprehensive cybersecurity program your team can maintain.
ISO/IEC 270013
ISO/IEC 27001 is an information security framework published as a joint framework by the International Organization for Standardization and the International Electrotechnical Commission. The last version of the ISO/IEC 27001 was published in 2022. The goal of the ISO/IEC 27001 is to provide requirements for an information security management system (ISMS). There are over a dozen standards in the ISO/IEC 27001 family, and organizations use this framework to manage the security of assets such as financial information, employee details, intellectual property, and information entrusted by third parties. Organizations can be certified by the accreditation body following the successful completion of an audit.
ISO/IEC 27001 requires that management:
- Systematically examine the organization's information security risks, taking account of the threats, vulnerabilities, and impacts;
- Design and implement a coherent and comprehensive suite of information security controls and/or other forms of risk treatment (such as risk avoidance or risk transfer) to address those risks that are deemed unacceptable; and
- Adopt an overarching management process to ensure that the information security controls continue to meet the organization's information security needs on an ongoing basis.
The ISO/IEC 27001 was designed to secure more than just IT. The SO/IEC 27001 was designed to provide a comprehensive information security management framework for organizations to follow.
.png?width=500&height=500&name=PDCA%2BCycle%2B(1).png)
Plan: Establishing the ISMS policy, objectives, processes, and procedures related to risk management and the improvement of information security to provide results in line with the overarching objectives and policies of the organization.
Do: Implement and utilize the ISMS policy, controls, processes, and procedures.
Check: Monitor and review the ISMS. Assess and measure the performance of the processes against the ISMS policy, objectives, and practical experience. Report all results to management for review.
Act: Update and improve the ISMS. Undertake corrective and preventative actions after the results of the ISMS internal audit is complete to ensure your organization continues to improve.
The ISO/IEC 27001 certification, like other ISO management system certifications, usually involves a three-stage external audit process defined by the ISO/IEC 17021 and ISO/IEC 27006 standards:
Stage 1: A Preliminary informal review of the ISMS is conducted. Checking the existence and effectiveness of key documents. For example, the maturity of the organization's information security policy, Statement of Applicability (SoA), and Risk Treatment Plan (RTP). This stage serves to familiarize the auditors with the organization and vice versa.
Stage 2: A more detailed and formalized compliance audit. This stage independently tests the ISMS against the specific requirements for ISO/IEC 27001. The auditors seek evidence to confirm that the information management system has been properly implemented and designed and is indeed in operation. They may complete this process by ensuring that a security committee or similar management body meets regularly to oversee the ISMS. Organizations that pass this stage are certified compliant with ISO/IEC 27001.
Ongoing: This process involves continuous reviews or audits to confirm that the organization remains compliant with the ISO/IEC 27001 standards. These audits or reviews may happen at least once a year, but can be conducted more frequently by agreement from management. This is especially important while the ISMS is still maturing.
CIS
CIS is the acronym for the Center for Information Security. The CIS Framework was originally developed in 2008 to help small and mid-sized companies cope with complex cybersecurity requirements. CIS Framework Controls are broken down into three categories. Basic controls, Foundational Controls, and Organizational Controls. CIS Controls are meant to apply easily to any industry or sector including healthcare, retail, finance, or government. The CIS Framework was created to, change the discussion from “what should my enterprise do” to “what should we ALL be doing” to improve security across a broad scale. You will notice that many CIS controls can be directly mapped back to both NIST and ISO.
The CIS guidelines consist of 20 key actions, called critical security controls (CSC), that organizations should implement to mitigate or block known vulnerabilities from attack. These controls are designed so that they can be automatically implemented, enforced, and monitored. The CIS security controls give easy-to-understand, actionable recommendations for cybersecurity. The CIS Consensus Audit Guidelines Goals include:
- Leveraging cyber offense to inform cyber defense, focusing on high payoff areas.
- Ensuring that security investments are focused to counter highest threats.
- Maximizing the use of automation to enforce security controls, thereby negating human errors.
- Using consensus processes to collect best ideas.
Basic Controls
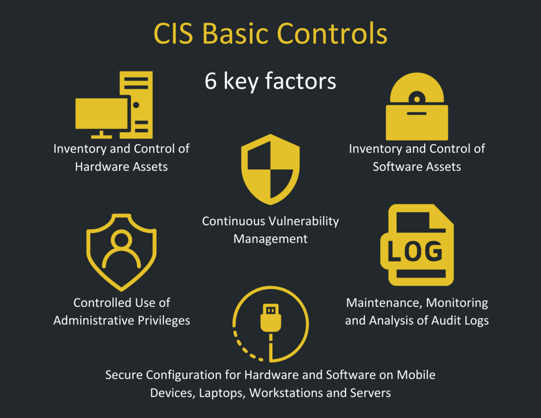
CIS Basic Controls consist of the following:
Inventory and Control of Hardware Assets: Your organization should know what computers and servers are running and what information they hold.
Inventory and Control of Software Assets: Software vulnerabilities are an extremely common vector for incidents and breaches.
Continuous Vulnerability Management: Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers.
Controlled Use of Administrative Privileges: The processes and tools used to track/control/prevent/correct the use, assignment, and configuration of administrative privileges on computers, networks, and applications.
Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers: Establish, implement, and actively manage (track, report on, correct) the security configuration of mobile devices, laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
Maintenance, Monitoring, and Analysis of Audit Logs: Collect, manage, and analyze audit logs of events that could help detect, understand, or recover from an attack.
Foundational CIS Controls:
Email and Web Browser Protections
Malware Defenses
Limitation and Control of Network Ports, Protocols, and Services
Data Recovery Capabilities
Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches
Boundary Defense
Data Protection
Controlled Access Based on the Need to Know
Wireless Access Control
Account Monitoring and Control
Organizational CIS Controls:
Implement a Security Awareness and Training Program
Application Software Security
Incident Response and Management
Penetration Tests and Red Team Exercises
The CIS Critical Security Controls are based around the tenet of “Offense Informs Defense.” Knowing what attacks have compromised systems in the past and how it was done can help inform your future offense actions; how to protect your system from future attacks.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for organizations that handle credit cards from major credit card companies. The PCI Standard is mandated by credit card brands but administered by the Payment Card Industry Security Standards Council. The PCI DSS was created to increase controls and security around cardholder data to help reduce credit card fraud. Basically, they want to ensure a minimum level of security when businesses store, process, and transmit cardholder data. If your company accepts credit card payments, it is vital that you meet PCI DSS compliance requirements. Otherwise, if your data is breached, your customer's information could become compromised, and your company will be held responsible. Unfortunately, 80 percent of businesses failed their initial PCI compliance assessment, according to Century Business Solutions. PCI DSS compliance is the new standard for credit card security, so it’s important that your business commits to meeting these security compliance requirements.
Validation of your PCI DSS compliance is performed based on the number of transactions your business processes.
- Self-Assessment Questionnaire (SAQ) — smaller volumes external
- Qualified Security Assessor (QSA) — moderate volumes
- Firm-specific Internal Security Assessor (ISA) — larger volumes; involves issuing a Report on Compliance
PCI DSS specifies twelve requirements for compliance, organized into six groups called "control objectives.”
- Build and Maintain a Secure Network and Systems
- Protect Cardholder Data
- Maintain a Vulnerability Management Program
- Implement Strong Access Control Measures
- Regularly Monitor and Test Networks
- Maintain an Information Security Policy
These are the 12 requirements for building and maintaining a secure network.
- Installing and maintaining a firewall configuration to protect cardholder data. Firewalls scan all network traffic and block untrusted networks from accessing the system.
- Changing vendor-supplied defaults for system passwords and other security parameters. These passwords are easily discovered through public information and can be used by malicious individuals to gain unauthorized access to systems. Your username and password should not be “admin” or “password.”
- Protecting stored cardholder data by encryption, hashing, masking, and truncation.
- Encrypting transmission of cardholder data over open, public networks through strong encryption, including using only trusted keys and certifications, which reduces the risk of being targeted by malicious individuals through hacking.
- Protecting all systems against malware and performing regular updates of anti-virus software. Malware can enter a network through numerous ways, including Internet use, employee email, mobile devices, or storage devices. Up-to-date anti-virus software or supplemental anti-malware software will reduce the risk of exploitation via malware.
- Developing and maintaining secure systems and applications. Vulnerabilities in systems and applications allow unscrupulous individuals to gain privileged access. Security patches should be immediately installed to fix vulnerabilities and prevent exploitation and compromise of cardholder data.
- Restricting access to cardholder data to only authorized personnel. Systems and processes must be used to restrict access to cardholder data on a “need to know” basis.
- Identifying and authenticating access to system components. Each person with access to system components should be assigned a unique identification (ID) that allows accountability of access to critical data systems.
- Restricting physical access to cardholder data. Physical access to cardholder data or systems that hold this data must be secure to prevent unauthorized access or removal of data.
- Tracking and monitoring all access to cardholder data and network resources. Logging mechanisms should be in place to track user activities that are critical to prevent, detect or minimize the impact of data compromises.
- Testing security systems and processes regularly. New vulnerabilities are continuously discovered. Systems, processes, and software need to be tested frequently to uncover vulnerabilities that could be used by malicious individuals.
- Maintaining an information security policy for all personnel. A strong security policy includes making personnel understand the sensitivity of data and their responsibility to protect it.
There are four levels of PCI Compliance based on the value of transactions you process annually, and the level of risk addressed.
- Level 1 – Over 6 million transactions annually
- Level 2 – Between 1 and 6 million transactions annually
- Level 3 – Between 20,000 and 1 million transactions annually
- Level 4 – Less than 20,000 transactions annually
Each business will have different needs and requirements based on a number of factors. If your business processes credit card transactions, we recommend consulting with a certified compliance specialist to ensure you are compliant with all the appropriate laws and regulations for your industry.
We hope this page has been helpful to you and your organization. Cybersecurity Frameworks provide organizations with the critical security standards they need to operate effectively and safely in today's digital age. Each security framework provides its own unique capabilities and challenges and can benefit organizations differently. If you or your organization needs help or advice implementing a cybersecurity framework, please contact info@celerium.com, and we will be happy to have our senior-level CISO answer any questions you may have.
Before you go,
If you'd like additional information on how to meet these frameworks, take a look at our cybersecurity resources page here: 50+ Cybersecurity Resources
